Power interruptions are among the top causes of IT downtime, equipment failure, and data corruption…
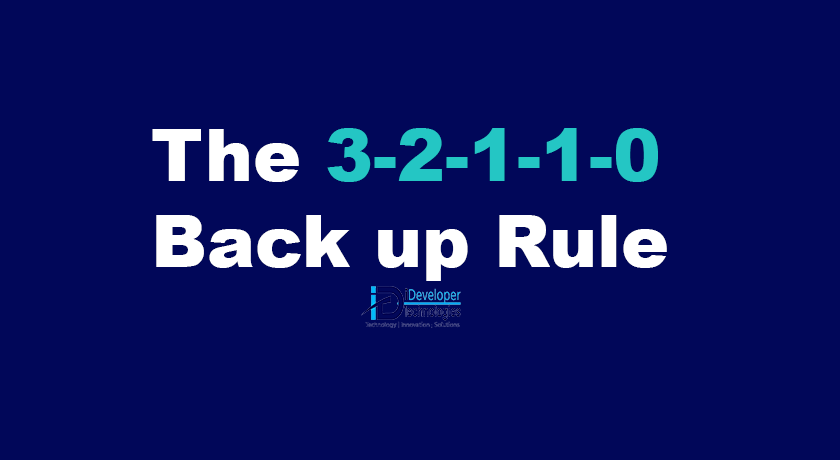
The 3-2-1-1-0 Backup Rule: Extend Your Backup Security
As cyberattacks occur more frequently and hackers develop new ways to access sensitive company data in order to benefit from it, the frequency of cyberattacks is continuously increasing.
According to Gartner experts, up to 75% of IT firms will experience at least one ransomware assault by 2025. Backups will probably be impacted by these attacks since hackers want to ensure that you can’t just restore your data without paying the ransom.
This implies that even the highest data protection standards may not be sufficient to truly safeguard the data. New techniques for protecting your data ought to be used. The 3-2-1-1-0 backup rule is one of these techniques.
The 3-2-1-1-0 Backup Rule: What Is It?
Five requirements must be fulfilled for the 3-2-1-1-0 backup rule to be in effect:
- A minimum of 3 copies of your data, including the production copy, should be in your possession.
- It is recommended to employ a minimum of 2 distinct storage media, such as a tape and cloud storage.
- In the event that your computers sustain physical damage, you should keep at least 1 copy off-site.
- If you would rather use the cloud, at least one copy should be immutable (i.e., cannot be altered in any way, under any circumstances) or maintained offline. Your backups ought to have finished without any issues.
With the highest data recoverability, this approach gives you the best defence against ransomware. You can restore your data and carry on working if there are no problems in your backups. No malware can access an offline copy over the Internet. You can utilise one copy off-site in case of an emergency in your workplace.
Three copies and two separate storages ensure that at least one will be accessible to assist you in returning to your job. In order to make an omelette in any case, the 3-2-1-1-0 rule advises against putting all your eggs in one basket.
The 3-2-1 and 3-2-1-1-0 Backup Rules’ Distinctions
The 3-2-1 rule was the industry standard until recently; businesses that were concerned about their data were abiding by it and thought they were doing well. However, backups need extra protection because ransomware assaults are becoming more frequent and have a propensity to focus more on backups.
3-2-1 and 3-2-1-1-0 backup rules differ in that the former aids in the preservation of your production data, while the latter offers all the features of its rival plus an additional backup-saving technique. The 3-2-1-1-0 approach greatly improves your chances of recovering your data regardless of whether your primary dataset is corrupted by virus, physically damaged, or human mistake. This is the greatest degree of protection
In conclusion.
Data security is a top priority for iDveloper Technologies Ltd., and we take every precaution to shield your data from ransomware and other threats so that it can be recovered in any situation. Please get in touch with us if you have any other queries.